Cybersecurity Requirements Specification for Public Network Connections Essential to Safety
The time it takes for cyber threat actors to find a new device online and attempt to compromise it, is minutes.
In a recent Area Maritime Security Committee and InfraGard Cross-Sector Council Meeting, I discussed that Houston and the surrounding areas may have important systems connected to the internet of which asset owners and systems operators may not be fully aware. While we do a fairly respectable job in keeping track and reaching out to inform those that appear either aware or unaware of the systems they have in or around (coupled) to their environment, we do find that new projects, new technologies being deployed, temporary staging for future in-process cutovers, tend to ultimately show up and expose systems with either vulnerable software, weak or default settings.
While in certain instances this may be temporary, the time it takes for cyber threat actors to find a new device online and attempt to compromise it is in minutes. In the maritime sector, things are seldom temporary and become permanent. It is important that our area works together and assign priorities to identifying our systems, third party systems that may be on the premise that connect to our systems directly or indirectly and understand the design and deployment of said systems. Identifying instances where a selected third-party integrator or vendor needs to perform and provide support through remote visibility and control which may be documented, however, security may or may not have been a firm requirement. We need to create a cybersecurity requirements specification (“CRS”) and for anything that must connect to a public network such as the internet.
Why is this important, you ask? Because in less than a five-minute search, we can find systems that are in our area and that are connected to the internet.
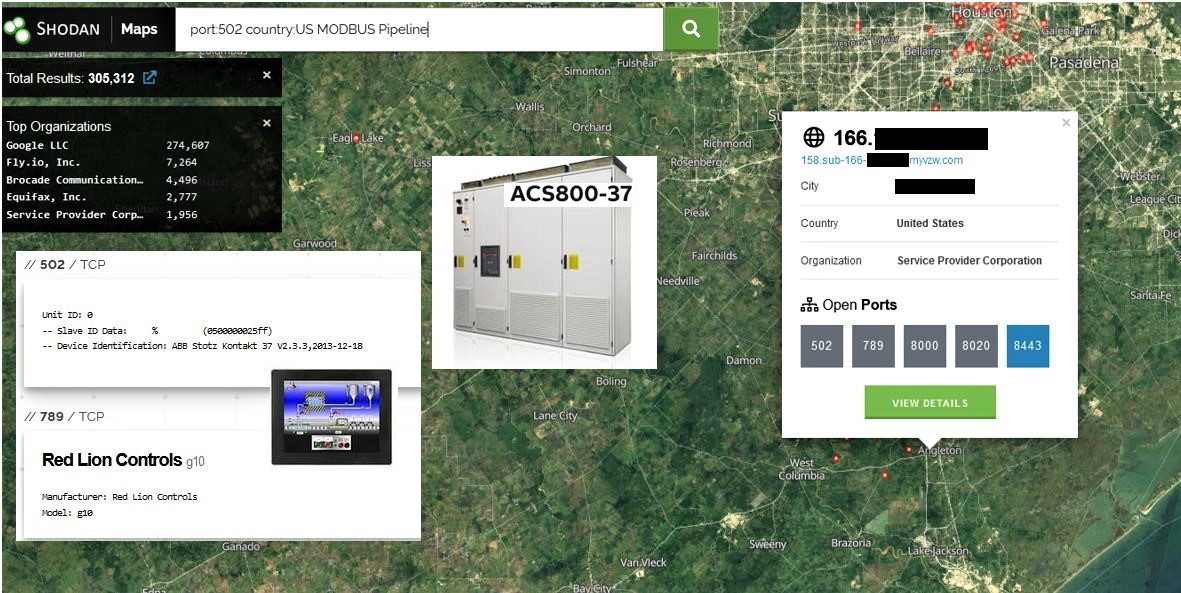 Example: Search of exposed control system connected to the internet in the surrounding area.
Example: Search of exposed control system connected to the internet in the surrounding area.
Reconnaissance web tools can aid and help play a crucial role in gathering information about computer and network hosts in our environment and in our area that are connected and potentially vulnerable. These tools operate by scanning the internet and identifying potential targets, making them a concern for various industries, including those with critical infrastructure.
At a high-level, reconnaissance web tools scan the internet and collect data about publicly accessible devices and services. They systematically search for open ports, exposed services, and other indicators that can reveal potential vulnerabilities. By focusing on specific areas such as camera systems guarding our ports and terminals, electronic badging systems, and control systems such as crane systems, product tank terminals and vessel load-out racks, these tools can provide valuable insights for security assessments.
Shodan.io is a popular reconnaissance tool known for its ability to search and index devices connected to the internet. It specifically excels in identifying vulnerable devices, including camera systems, electronic badging systems, and maritime control systems. Shodan.io scans IP addresses and gathers information about open ports, services, and banners, allowing users to search for specific devices or vulnerabilities. For example, one could search for camera systems used in maritime ports and terminals to assess their security configurations. Its vast database includes information on a wide range of systems, including cameras, servers, routers, and other network devices. By leveraging advanced search queries, Shodan.io allows users to locate specific camera systems guarding maritime ports and terminals, electronic badging systems, and maritime control systems. Malicious actors can misuse this information to identify vulnerable targets for potential exploitation by utilizing weaknesses in these systems to disrupt port operations, compromise security, or cause economic damage and a logistical nightmare.
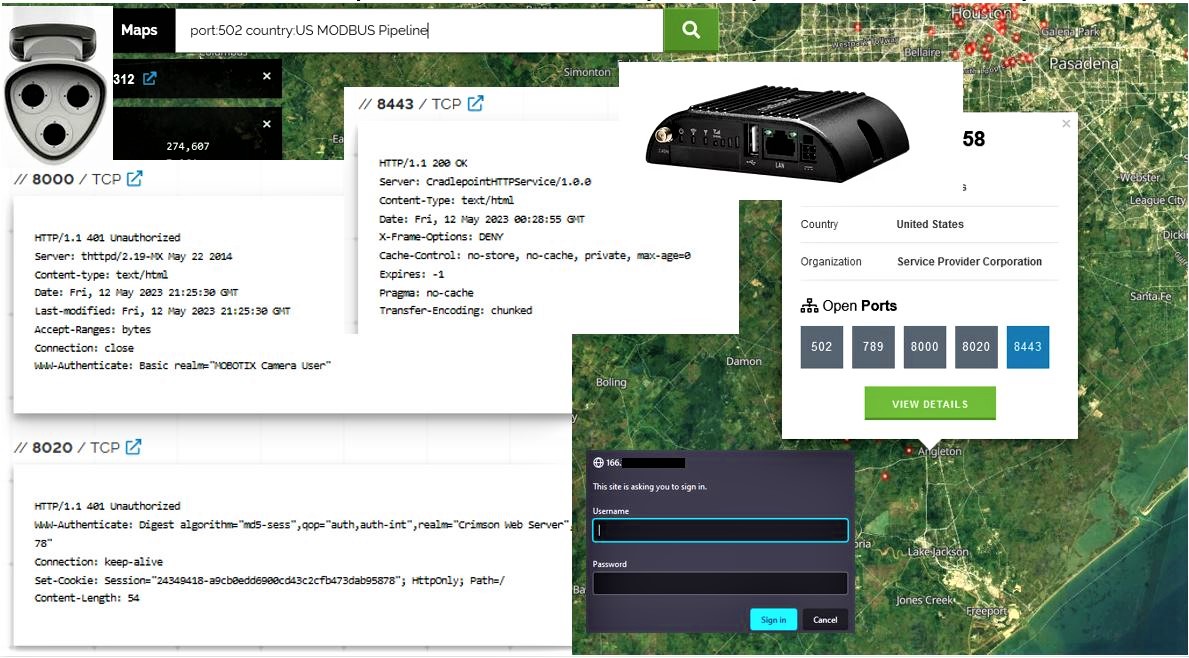 Example: Search of exposed control system connected to the internet in the surrounding area.
Example: Search of exposed control system connected to the internet in the surrounding area.
It is important to note that scanning the internet using tools like shodan.io is not illegal. In fact, such scanning is often performed as part of security assessments to identify potential risks and vulnerabilities. However, it is crucial to respect the boundaries of legal and ethical considerations. Unauthorized attempts to exploit or gain unauthorized access to devices or systems discovered through scanning can be illegal and unethical. It is essential to obtain proper consent and adhere to legal guidelines before diving deeper into specific devices or systems found during the reconnaissance process. If it is not your fully owned system(s), then do not proceed any further other than identification.
One other finding is cameras that are connected to the internet within our area. Over 18,000 cameras in the Houston area are public facing and could have vulnerabilities and ease of access. Asset owners and system operators need to confirm and make certain they have identified and documented their camera systems and what is connected to the internet and work with the IT security leads in their company to secure these systems preferably behind a secure perimeter firewall system and deploy multifactor authentication or MFA.
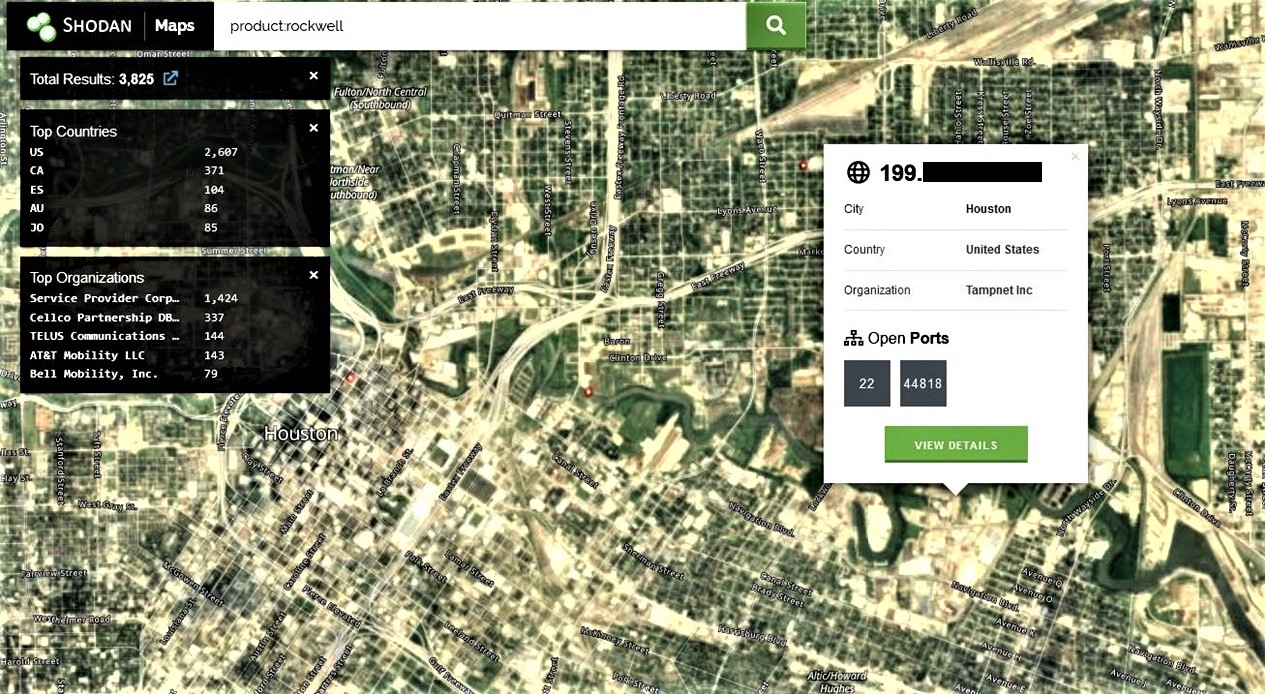 Example: Search of exposed control system connected to the internet in the Houston Ship Channel area.
Example: Search of exposed control system connected to the internet in the Houston Ship Channel area.
Results based on the search of connected Hikvision cameras: Houston is number #1 in the U.S. followed by New York, Chicago, Miami, Philadelphia, and Los Angeles. All have ports, terminals, and other critical infrastructure.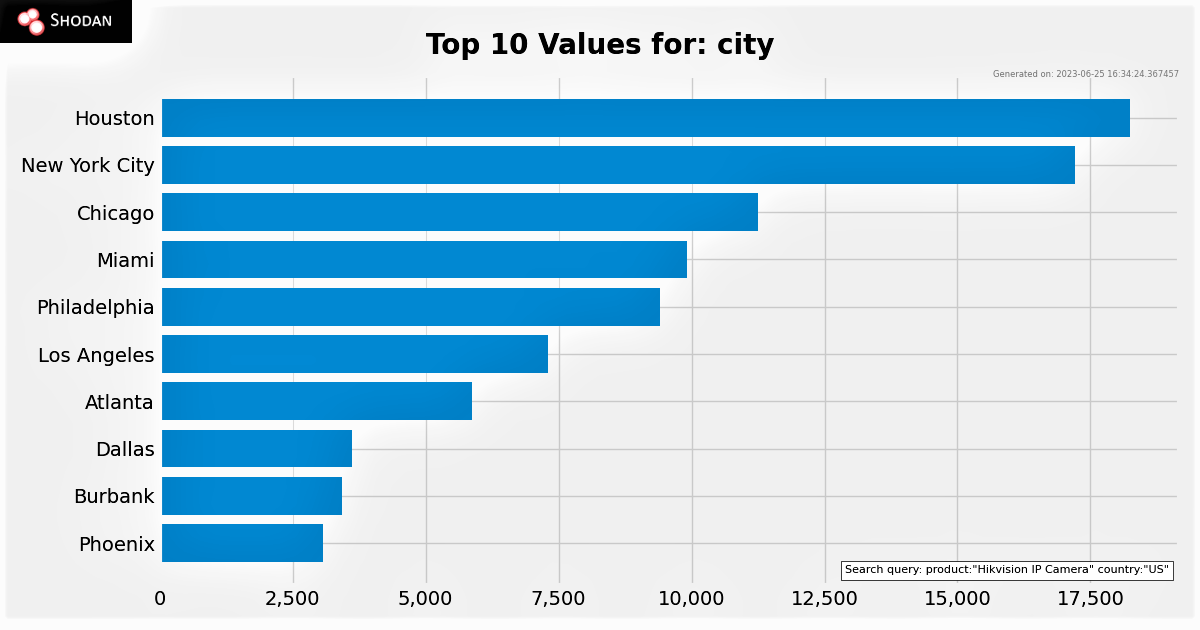
The FCC placed ban authorizations for devices that pose a national security threat to federal buildings and national security grounds in 2022.
Security cameras help in ensuring the safety and protection of critical infrastructure environments in our area. Deploying security cameras in these environments allows for constant surveillance, threat detection, and incident response, thus enhancing overall security. Allowing remote view and monitoring capabilities further augments the effectiveness of security cameras in critical infrastructure. With remote access, authorized personnel can monitor the premises and respond promptly to any suspicious activities or emergencies from a centralized location. This remote capability enables real-time situational awareness and facilitates timely decision-making, improving the efficiency and effectiveness of security operations.
However, connecting these security camera systems to the public internet introduces various obstacles and security hangups that need to be carefully addressed in all instances. From the asset owners’ perspective, the primary concern is maintaining the surveillance cameras confidentiality, integrity, and availability of the system. Ensuring secure connectivity, strong authentication mechanisms, and encryption protocols is crucial to prevent unauthorized access, data breaches, and tampering of video feeds. Asset owners need to establish robust network segmentation and access controls to limit exposure and potential attack vectors. Network segmentation is a regulatory requirement in particular sectors.
From the perspective of a cyber adversary, the connection of critical infrastructure systems to the public internet provides potential entry points for exploitation. Cyber threat actors may attempt to infiltrate the surveillance system to gain unauthorized access to other critical infrastructure or extract sensitive information. Threat actors could employ various tactics, such as exploiting vulnerabilities in the camera firmware, leveraging weak passwords, or launching sophisticated attacks like phishing or malware injection.
Once inside the system, they can disrupt operations, manipulate video feeds, or use the compromised cameras as a foothold to launch further attacks on the infrastructure. In field vulnerability and risk assessments performed around one vector into the enterprise and operation technology environment has been through misconfigured camera systems, firewalls, and exposed public internet access.
Overall, the need for security in operational technology, cameras, and badging systems in critical infrastructure environments is indisputable, and remote view and monitoring capabilities further enhance their effectiveness. However, the obstacles and security hangups associated with connecting these systems to the public internet require diligent attention and robust security measures from employers to safeguard against cyber adversaries who seek to exploit vulnerabilities for their malicious intents.
The Area Maritime Security Committee and InfraGard Cross-Sector Council meet monthly, and we would like to encourage you to join the committee. This group is primarily focused on the physical and cybersecurity aspects of our area pertaining to maritime, oil & gas, and petrochemical sites in and around the Houston Ship Channel. If you or someone you delegate wishes to join, please reach out to me at my contact information below.
About the Author
 Marco Ayala, marco.ayala@infragardhouston.org
Marco Ayala, marco.ayala@infragardhouston.orgSector Chief Maritime Domain CSC-InfraGard
AMSC HOU-GALV Cybersecurity Subcommittee Chair
AMSC OCS GOM Cybersecurity Threat Analysis Subcommittee Co-Chair
Marco Ayala is global director of cybersecurity at 1898 & Co., and an instructor and vice president-elect for the International Society of Automation. With more than 25 years of experience, he focuses on the safety and security of industrial automation and control systems(IACS) in the maritime domain, and for oil and gas, chemical and maritime entities around the globe.
