The Importance of Collaboration in the Physical and Cybersecurity Threat Landscape

Texas is home to some of the busiest and most important maritime ports and terminals in the United States. From the ports of Houston, Texas City, Galveston, and Freeport to the Port of Corpus Christi, including the vast array of Houston ship channel petrochemical operators, these facilities play a vital role in the state's economy and the country's supply chain. They handle a wide range of cargo, including oil, natural gas, chemicals, and other goods.
As with any critical infrastructure, the security of these ports and terminals is of utmost importance. In recent years, there has been an increased focus on both cybersecurity and physical security at these facilities.
Great strides have been made in technologies that our Houston area has adopted and embraced. This has aided and streamlined everything from operational awareness, business intelligence and analytics, including how both physical security and information technology as well as automation systems have become more intertwined and converged. The speed at which we, as an industry, have adopted and deployed new technologies in our facilities far outpaces the speed in which elements of cyber-informed engineering was considered at the front-end engineering designs (“FEED”). This in itself has created some hybrid vulnerabilities that can be complex when using systems that are insecure by design. Much of this can be attributed to backwards compatibility but even more so with the integration to external environments such as cloud computing and other third-party services that create vectors of unverified trust into a plant or ports operations.
Ports and terminals are vulnerable to cyber-attacks, which can disrupt operations and have serious economic consequences. On December 25, Christmas Day, the Port of Lisbon (Porto de Lisboa) was the target of a ransomware attack claimed by the LockBit gang. LockBit is a ransomware gang that has been active since at least 2019. The group is known for using ransomware to encrypt the data of victim organizations and demanding payment in exchange for the decryption key. The group has targeted a wide range of organizations, including healthcare providers, local governments, and schools. There is limited information available about the individuals behind the LockBit gang, and it is not clear where they are based. The Port of Lisbon confirmed that the cyber-attack did not compromise operational activity; however, attackers have laid claim that they have stolen financial reports, audits, budgets from everything from cargo and crew details to emails and personally identifiable information (“PII”), threatening to publish if not paid $1.5 million in currency.
In August of 2021, Port Houston quickly identified an attempted intrusion into their business systems and were able to isolate the system while working with their security vendors and local federal agencies. The attempt used what is known as a zero-day exploit which is an undocumented or publicly known vulnerability in software and hardware in which detection algorithms or patches do not exist for the vulnerability. It is very important to note that Port Houston was lucky that they took the anomaly they had and questioned it while confirming and escalating, then pulling the plug on the adversary’s attempt. It could have been missed as per a presentation given by Chris Wolski at the 3rd Port of the Conference in Houston in April 2022.
In 2019, the Carnival Corporation, the world's largest cruise line operator, announced that it had experienced a data breach affecting the payment card information of some of its guests and employees. More recently, in 2020, the shipping company CMA CGM suffered a cyber-attack that disrupted its operations for several days. These are just a few examples of the types of cyber security incidents that have affected the maritime shipping industry. There have been several other reported incidents of cyber-attacks on ships and ports, including the targeting of vessels with malware, phishing attacks, and the exploitation of vulnerabilities in shipboard systems. It is important for the maritime industry to take steps to improve cyber security and protect against these threats.
We must ask ourselves if incidents like all of these could be a “sleight of hand twist of wrist” for foreign military operations to embed or drop other payloads such as zero-days for later uses. We have to start thinking like an adversary but even more importantly, think like an engineer in the design detection and protections of both physical and cybersecurity. Think, prepare, plan multiple threat vector events, and exercise them annually. Bringing in external consulting to facilitate the scenarios is very helpful to keep this from becoming a “check the box” exercise.
To protect against these threats, ports and terminals must implement sound cybersecurity and physical security measures. Today, in-depth defense strategy begins with protecting our ports and terminals by ensuring that they have strong physical security measures in place. This includes measures such as fencing, gates, and guards to prevent unauthorized access to the facility. It is also important to have security cameras and other surveillance equipment in place to monitor activity within the port or terminal. An emerging threat to port and terminal security is the use of drones. Drones have the potential to be used for both malicious and innocent purposes, but they can pose a threat to the security of a port or terminal if they are used to transport contraband or to conduct surveillance on the facility. To combat this threat, many ports and terminals have implemented drone detection and mitigation systems, which use radar and other technologies to detect and track drones in the area.
In addition to physical security measures, it is also important that ports and terminals have robust cybersecurity measures in place. This includes measures such as firewalls, antivirus software, backups, multifactor and encryption to protect against cyberattacks. It is also important to regularly update these measures and to train employees on how to identify and prevent potential cyber threats.
One area where ports and terminals are particularly vulnerable to cyberattacks is through their supply chain. Many ports and terminals rely on third-party logistics providers and other partners to manage the flow of goods in and out of the facility. These partners may not have the same level of cybersecurity protection as the port or terminal, leaving them open to potential attacks. To mitigate this risk, ports and terminals should ensure that their partners have strong cybersecurity measures in place and should regularly assess the security of their supply chain.
Another potential vulnerability for ports and terminals is the use of Internet of Things (“IoT”) and Industrial Internet of Things (“IIoT”) devices. These devices, which are connected to the internet and can be used to control and monitor various systems within the facility, can potentially be hacked and used to disrupt operations or steal sensitive data. To protect against this threat, ports and terminals should ensure that they have strong cybersecurity measures in place for their IoT devices and should regularly update and patch these devices to prevent potential vulnerabilities.
Tracking Local Threats
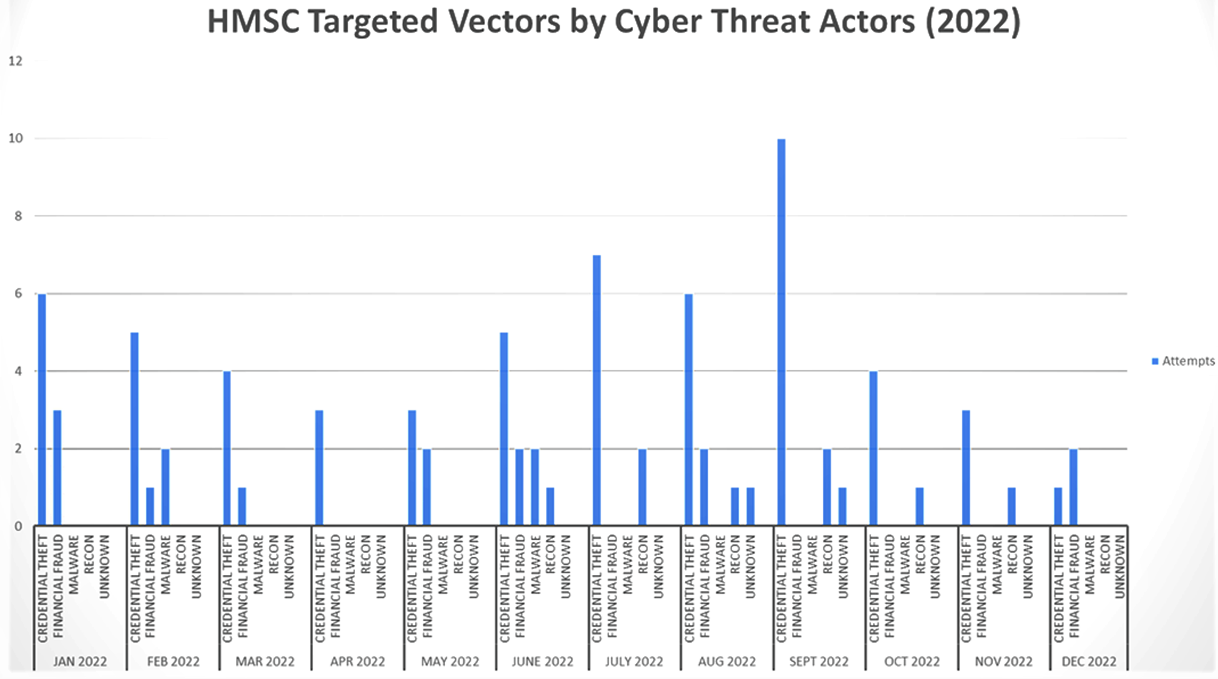
In addition to tracking of physical threats, our area has been tracking threats from cyber adversaries that are actively probing our systems. These targeted vectors span the year, were primarily delivered via email, and cover the following types:
- Credential Theft. Credential theft is an attempt to acquire someone’s login credentials
- Financial Fraud. Illegal manipulation or deception of financial transactions for personal gain.
- Malware. Malware is malicious software designed to harm or exploit computer systems.
- Reconnaissance. Investigating and gathering information about a facility physically by social engineering (including cameras, drones, etc.) or through a computer network.
- Unknown (MISC). Threat actor’s objective cannot be determined due to limits in analysis and response tracking.
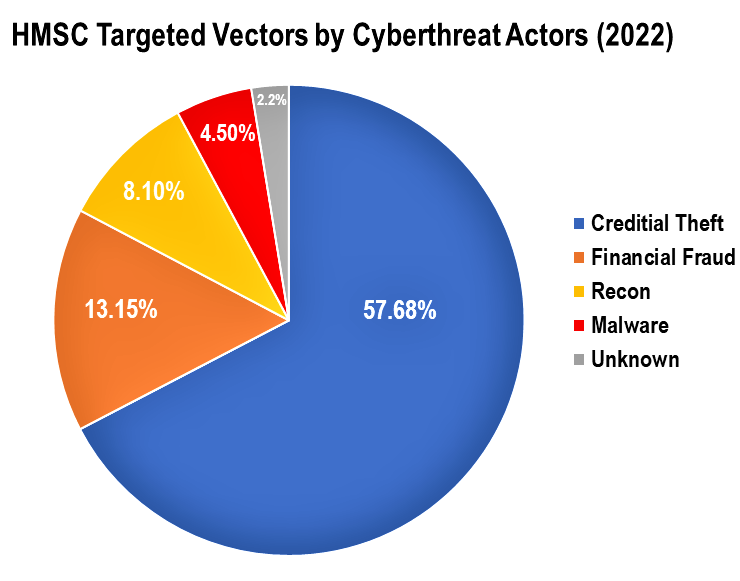
The year led with 57 total credential theft attempts, followed by 13 financial fraud attempts, 4 malware payloads, 8 reconnaissance attempts, and 2 unknowns that our area port infrastructure and local industry reported to the Houston Maritime Security Collaboration group (“HMSC”). The HMSC is a group of people representing ports and terminals, including refining and chemical companies from Houston down to Corpus Christi that are vetted and that share alerts through secure means. This group can be joined by members of InfraGard and Houston Ship Channel Security District members that are in the need-to-know that play part in both the physical and cybersecurity affairs of their companies.
Overall Takeaways
 In addition to cybersecurity measures, it is also important that ports and terminals have strong contingency plans in place to respond to potential cyberattacks. This includes having a team of physical and cybersecurity experts on hand to identify and respond to threats, as well as having backup systems in place to ensure that operations can continue in the event of an attack.
In addition to cybersecurity measures, it is also important that ports and terminals have strong contingency plans in place to respond to potential cyberattacks. This includes having a team of physical and cybersecurity experts on hand to identify and respond to threats, as well as having backup systems in place to ensure that operations can continue in the event of an attack.
Overall, the protection of our maritime ports and terminals is crucial for the state’s economy and national security. By implementing strong physical security measures, such as drone detection systems, and robust cybersecurity measures, including strong supply chain security and contingency plans, ports and terminals can ensure that they are prepared to respond to any potential threats.
If you are interested in joining the InfraGard Cross Sector Councils (“CSC”) or the HMSC, please reach out to me for more information and how to apply.
By working together we can increase our awareness and response times dramatically compared to years ago. This group has made great progress and can always use more expertise. Also, anyone needing a risk assessment for their site, please email me at marco.ayala@1898andCo.com so we can do a site review.
If you are interested in joing the InfraGard CSC or the HMSC, please email marco.ayala@infragradhouston.org for details or more information.
About the Authors
 Marco Ayala, marco.ayala@1989andco.com
Marco Ayala, marco.ayala@1989andco.comMarco Ayala is the Cybersecurity Chair of the AMSC and InfraGard Sector Chief of the Maritime Domain with over 27 years of experience working in petrochemical facilities, where he designed, implemented, and maintained their process instrumentation, automation systems, and process control networks. He is the Global Director and ICS cybersecurity Sector Lead with 1898 & Co. part of Burns & McDonnell Engineering Company.
With 19 years in industrial cybersecurity, he has led efforts to secure the oil and gas, maritime port, offshore facilities, and chemical sectors, supporting federal, local, and state entities for securing the private sector. Marco is the International Society of Automation Vice President-elect for Automation and Technology.

Larry Medrano is an InfraGard Deputy Sector Chief, Maritime Cyberscurity & Threat Intelligence, with over 9+ years of IT experience in the government sector. He is responsible for overseeing the development, implementation, and continued advancement of the cybersecurity program for the Port of Corpus Christi as their acting Cybersecurity Manager.
